Behind the "killing" of big data is how to keep up with the abuse of personal information.
CCTV News:Entering the era of big data, I believe many people have this experience, not the tourist season, but the ticket price is getting higher and higher; When chatting, I casually mentioned a certain product, and when I turned around, I saw the advertising push of related products on major platforms. In the Internet age, we can quickly find the information we want, but the information and data about ourselves seem to be more easily leaked or illegally used by businesses without our knowledge. The following is a case in which consumers are "killed" by big data.
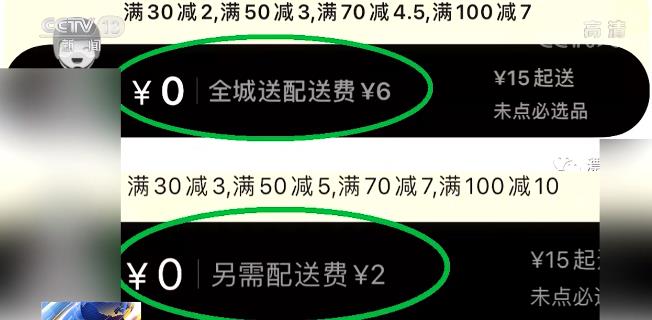
Not long ago, an article that questioned the use of algorithms by a take-away platform to "kill cooked food" sparked heated discussion. A member user of the platform pointed out that his delivery fee is often higher than that of non-member users for the same order. What was going on at that time? The reporter contacted Mr. Xiao, the author of this article.
Mr. Xiao:"I often order the same takeaway, and suddenly one day I opened a member and found the delivery fee price.Compared with beforeIt has tripled in one fell swoop. It used to be two yuan or free, and then I tried it for almost an hour from 12 noon to 1: 30 pm that day, and the delivery fee was always higher than usual, which was six yuan at that time, and then suddenly caught my attention. "
Mr. Xiao told reporters that in the following week, when ordering takeout, he often used two mobile phones at the same time to log in to member accounts and non-member accounts for comparative experiments, and found that the difference in delivery fees always existed. So he summarized these observations into an article and published it in his personal WeChat official account.
Mr. Xiao:"Later, after my article came out, many netizens left messages in the background and met this kind of member ‘fool friends or acquaintances in business’ The situation. For example, a single item and a mouse, I bought it in 100 yuan when I was not a member, but I bought it with a member.The price became 110 yuan. After I open a member, the price is higher than that of a non-member, so what is the significance of my opening a member? "
After the article sparked a heated discussion, the relevant take-out platform contacted Mr. Xiao. In response to his query, the platform gave the reply that the price difference in delivery fee was an error caused by system cache.
Mr. Xiao:"I have tried many times, and this is the case within a week. That cache statement certainly doesn’t make sense.Where is the location cache? In the same place, the difference is between members and non-members. I consulted some technical friends, and it is true that the error of this cache is within five meters, but it is impossible to cause such a big error. "
Mr. Xiao’s doubts finally failed to get a clear answer. However, his experience has brought the topic of "killing" big data into the public’s field of vision again. So what is behind the "killing" phenomenon of big data?
360-degree accurate portrait The platform collects a lot of personal data.
According to experts, the most critical step in killing big data is to be very familiar with customers, and thus provide differentiated choices. This has already existed in some previous business models, and there are few negative comments.
Pei Wei, Associate Professor, Beihang University School of Law:"As far as big data killing itself is concerned, it is actually differentiated pricing behind it. For example, in insurance, different people may guarantee the amount or amount of money, or the compulsory period of insurance will be different. Therefore, if we simply use differentiated pricing, it does not necessarily constitute a negative thing. What we are disgusted with is differential pricing without a legitimate basis. "
According to China Consumers Association, consumers are interested in big data.“The core of the problem is the application of algorithm technology on the Internet platform, which is embodied in recommendation algorithm, price algorithm, evaluation algorithm, ranking algorithm, probability algorithm and traffic algorithm.
Jian Chen, Director of Complaints Department of China Consumers Association:"For example, when a consumer buys goods or services, the platform will form some personalized recommendations for him according to some browsed pages of the consumer or some preferences of the consumer, including his whereabouts. In fact, the operator may have made some accurate personal data portraits of consumers. According to this portrait, the relevant goods and services are only recommended to him, so his right to know is very flawed. "
How is the Internet platform "familiar" with every user? The answer is through user portraits. Behind the accurate user portrait is a large amount of personal data accumulated by the platform.
Liang Zheng, Vice President of Tsinghua University Institute of Artificial Intelligence International Governance.: "With my data, you finally made such a portrayal of me. Is this accurate? If it is too accurate, people will worry about being manipulated. After a little in-depth discussion, I will find that what I care about is its own discriminatory pricing, or is my information reflected behind it improperly collected and used? "
"APP eavesdropping" technology can be realized, but the cost is high. Low efficiency and high legal risk.
User portraits based on big data can let merchants find out whether you like spicy food or sour food, and rank restaurants that are more in line with your taste through algorithms. User data is often collected by the Internet platform through one mobile APP. In the process of dealing with these APPs, there are also problems that worry everyone, such as the phenomenon of "APP eavesdropping" that we often hear. So does "app eavesdropping" exist?
The APP Governance Working Group consists of a group of cyber security legal and technical experts from the National Information Security Standardization Technical Committee, China Consumers Association, internet society of china and China Cyberspace Security Association.
Technical experts first demonstrated to us whether the APP can eavesdrop technically and what might happen if it eavesdrops through a simulated "APP eavesdropping test program" developed by them.
"We will now enter this test. If we make a speech like this, what happens when the hand is released? The recording actually continues. In fact, we can remove this hint, and the whole process of the test is two minutes. "
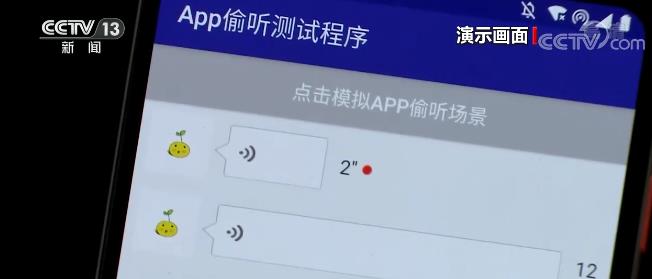
Two minutes later, we can see that a 120-second speech was generated in the test program. After the technicians export the voice data, after checking, it is confirmed that "eavesdropping" can be realized when the test program is placed in the foreground.
In addition, after a comparative experiment, the technician told us that the recording can continue for a period of time when the test program is back to the background or the mobile phone is locked, but it will terminate automatically. Just different mobile phone operating systems, the duration of continuous recording under lock screen is slightly different.
Then, is the technically achievable "eavesdropping" method abused in the APP on the market?
Expert of APP Governance Working Group He Yanzhe:"When we actually do this kind of detection of eavesdropping, we found that we haven’t found any APP that has this eavesdropping behavior after uploading voice information."
According to experts from the APP Governance Working Group, although it is technically possible to sneak shots and sneak recordings, this method is costly, inefficient and has high legal risks.
Experts from the APP Governance Working Group said that at present, both the industry standard and the technical level are further strengthening the transparency of calling sensitive rights such as mobile phone microphones, so as to let mobile phone users know.
Expert of APP Governance Working Group He Yanzhe:"Now we see that there are some mobile phone operating systems that have realized real-time prompts for the use of microphones. We call it a recording indicator, which means that when you want to call this microphone, there is a status bar, a red dot or a reminder. "
Accurate platform recommendation is the result of multi-channel aggregation accumulated all the year round.
I just chatted with my friends about the fitness plan, and in a blink of an eye, online shopping platforms began to recommend fitness products to you; Or search for the bottom materials of the overheated pot on a platform, and many platforms have started to recommend the ingredients of the shabu-shabu and even the pots and pans to you frequently. How is such an accurate personalized recommendation achieved?
Expert of APP Governance Working Group He Yanzhe:"An APP, we say that it can make a 360-degree portrait of a user. This portrait, I believe, is the result of years of accumulation, which is the first; Second, it is the result of convergence of multiple channels. "
According to experts, the accuracy of the portrait is mainly achieved through big data analysis of our purchase records, browsing records, search records, and even downloaded application lists.
Expert of APP Governance Working Group He Yanzhe:"Why do you say that sometimes you feel eavesdropped? Providing this source of big data, it is not the current APP, it may be other apps. You have done some operations, it will aggregate the corresponding information together, and it may also associate your friends and people in the same area. Then they have some actions, and it may also become a direction for it to push advertisements. "
Experts suggest that users can find the microphone permission in the permission settings of the mobile phone operating system and check which apps are currently authorized to use the microphone. According to their own needs, users can turn off the authorization to use the microphone for the APP at any time.
More attention should be paid to the illegal collection of personal information by APP.
When the experts of the APP Governance Working Group tested the APP on the market, they also found many problems, such as the long privacy policy, the difficulty for users to understand and the inability to cancel accounts.
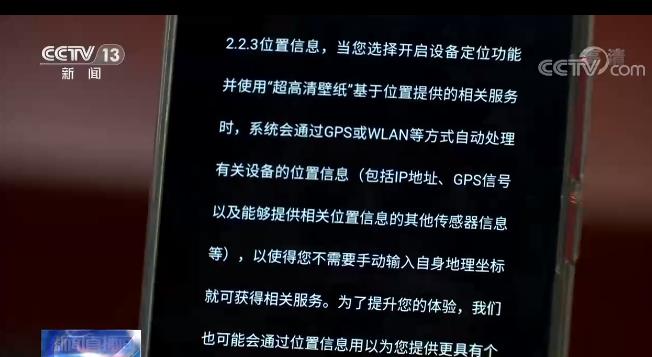
"Let’s give an example. In the process of testing, we found that this wallpaper APP has a privacy policy of more than 10 thousand words. Then let’s see what it says. I believe that no one will finish reading this privacy policy. Even people like us who read privacy policies every day have a headache. For example, this location information written in this privacy policy. The APP said that I want location information. It said a lot of reasons, but I don’t think this reason has anything to do with wallpaper. "
Pei Wei, Associate Professor, Beihang University School of Law: "Whether the privacy policy really serves users or really protects individuals is actually a broken state. Therefore, what is more worrying in the future is the formalization of this protection. "
The APP Governance Working Group has a WeChat WeChat official account platform for "APP Personal Information Reporting" and a dedicated reporting mailbox. Experts told reporters that the difficulty of account cancellation is another problem with a large number of complaints from users at present.
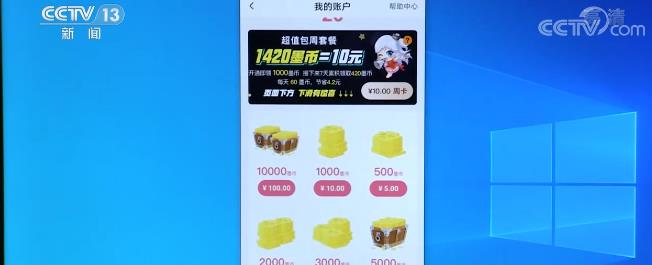
"Take a look at this APP first. There is an account cancellation function. I click to enter my information, and then I find the following sentence is ‘ There is ink balance in the account. Cannot cancel ’ . After I clicked on it, I found that there were 20 virtual coins, which were given by me when I newly registered, and I didn’t buy them myself. I thought, can I use it? It says 49 ink coins. But I only have 20, that is, I have to make up the money, and I will never be able to divide that number. So I can never cancel it. "
Ding Xiaodong, deputy dean of the Institute of Future Rule of Law of Renmin University of China: "From the research of information law, we often have a term called ‘ Digital branding ’ . In this network society, all the footprints are permanently marked. In our country’s personal information protection law, there is a special provision. We say that from the legal rights and interests, it belongs to an individual’s right to delete. "
Pei Wei, Associate Professor, Beihang University School of Law:"The national standard for information technology security, which involves the personal information security specification, specifically mentions this cancellation. That is to say, when you log off or stop using a certain service, its ways and means should be the same as when you use this service. Then at the same time, the information you are required to provide during the logout process should not be more than the information you use and the identity information you provide when using the App. "
According to experts, the collection of personal information is only one of the links in the circulation of data elements. Protection of personal information security, data storage, processing and circulation also need attention.
Ding Xiaodong, Vice President of the Institute of Future Rule of Law of China Renmin University:"If the front-end link (data collection) is closed, it will actually have a great impact on the development of artificial intelligence and data industry. Then how to reconcile? I think a very important aspect is that after the collection of personal information, it must be managed in a very strict life cycle. We should have an anonymous mechanism and a fuzzy mechanism. When processing, we may have to adopt some principles of data minimization to process the necessary data. In particular, a very high standard should be adopted in the aspects of storage and circulation and the protection of leakage. "
The security boundary needs to be explored by the users of the regulatory platform.
Nowadays, the convenience brought by technology and the protection of personal information are at the two ends of a swinging balance. What role does the law play in the process of "balancing" this balance?
Ding Xiaodong, Vice President of the Institute of Future Rule of Law of China Renmin University:"Our traditional consumer protection law also includes the application of contract law to standard terms, the application of tort law to infringement issues, and many problems in administrative supervision. All these laws can be invoked to a certain extent. But on the other hand, many problems are caused by new technologies such as personal information and algorithms, so to some extent, there are still some shortcomings, and the legislature is actively following up. The entry into force of our civil code may provide a lot of legal support for the protection of personal information. Then the formulation of the Personal Information Protection Law (draft) and the Data Security Law (draft) will certainly provide a lot of additional protection in the future. "
Nowadays, each of us is producing a lot of information. Experts said that in the current social life driven by algorithms and big data, the law plays more of a role of protection. The delineation of security boundaries needs to be explored by regulators, platforms and users in interaction.
Liang Zheng, Vice President of Tsinghua University Institute of Artificial Intelligence International Governance: "From the perspective of laws and regulations, it should be the bottom, and then we draw some red lines, which cannot affect public safety. Even some business models like the digital economy are iterative very quickly, and we can’t wait until the law is enacted. For each problem, there can be corresponding technical solutions to deal with it. It is not unsolvable. The key is that we should make the rules clear. "